

Inspiration Corner
A collection of write-ups from experiences of life that inspire, empower, influence & trigger positive values, habits & mindsets.
Cricket, Hockey and Baseball - each game is played between two teams where a solid sphere is the object of a contention,
battered using wooden batons and chased by players across the field.
Nonetheless, there are similarities and competition enjoyed by participants as well as onlookers; however, each sport is different from the rest and has its own characteristics. Wouldn't you call it a blunder if someone confuses one of these sports with the others or uses their names interchangeably?
Well, that is the kind of mistake most computer users make when there is a topic about computer viruses, worms, trojans, malwares and so on.
Nonetheless, there are similarities and competition enjoyed by participants as well as onlookers; however, each sport is different from the rest and has its own characteristics. Wouldn't you call it a blunder if someone confuses one of these sports with the others or uses their names interchangeably?
Well, that is the kind of mistake most computer users make when there is a topic about computer viruses, worms, trojans, malwares and so on.
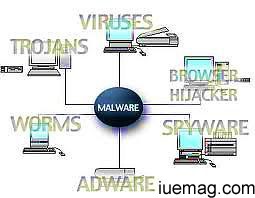
Many people don't even know if there is a difference between these terms and use them interchangeably.
In case you find yourself guilty of such gaffe, worry not; just read on and if you are one of the apprised ones,
please correct me if you find something missing or incorrect.
Let's start with malware. You may relate it to the word sport mentioned in the analogy above. Just as sport is an umbrella term that covers Cricket, Hockey, Baseball and so on, malware is the word that covers computer viruses, worms, Trojan, spyware, rootkit etc. In simple words, Malware is any malicious program or software designed to exploit a computer user.
A Virus in the human body is an organism that replicates itself, overwhelming body's defense mechanism and making it sick. Similarly, a program qualifying to be a computer virus must be able to replicate and execute itself. Almost all the viruses are attached to some executable file and may not affect your system unless you run or open the file. Some viruses are programmed to damage the computer by damaging programs, deleting files, or reformatting the hard disk. Others are not designed to do any damage, but simply to replicate themselves and make their presence known by popping text, video, or audio messages, which keep troubling the users. Viruses cannot spread without a human action and require transfer of an infected host file to another system for spreading.
Worms, on the other hand, are capable of spreading without human action. A worm seeks network loopholes and takes advantage of file-transport or information transport features that allow it to travel on its own. Like viruses, worms replicate themselves within a computer system but unlike viruses, a worm doesn't have to attach itself to a program. Also, worms generally localize their damage to the computer network by causing increased bandwidth.
A Trojan doesn't replicate but is as full of chicanery as the mythological Trojan Horse (of Troy). It appears to be a safe and useful piece of software but hidden inside is something harmful. While running, it may pretend to be doing something useful in the foreground but in reality, they shall work silently in the background damaging your system and/or stealing the data.
In addition to these, there are other malwares like Spywares that without your knowledge, collect your information and send it to someone who can use it.
Scarewares, which appear to be a free antivirus application but on installation proceeds to tell that system is infected with hundreds of viruses and can be cleaned only if you pay for full version.
Blended Threats, which are more sophisticated attacks bundling the worst bearings of worms, viruses and Trojans into a single threat.
Rootkits, which are designed to gain root oradministrative access to your system. I would not contempt your imagination by mentioning what harm rootkits can do.
There are more and the list keeps growing. Now you must be clear with the above mentioned terms. However, you also need to be aware of what you can do to protect yourself. Humans are generally the weakest link in the chain and unknowingly get systems affected. A little care can help you be safe, which is certainly better than being sorry. Do not click the links you are not sure about. You may install addon like WOT in your browser (firefox/chrome) which helps in identifying if a link is safe. Do not accept suspicious files or files from unknown people. Some email programs allow a "peek" into the files. Avoid even that for such files. While downloading software from internet, make sure it is from some reputed site like sourceforge or cnet.
Keep your operating system patched with latest updates. Especially if you are using Windows, get a good antivirus program and keep it updated. Don't let your firewall down. Disable auto-run in your system. Back up your important data regularly.
Share the same with your near and dear ones and if you have any more easy-to-follow points, feel free to add them to the list and mail us. We shall pass the same to the other readers of IU e-Magazine.
That's it for now. Don't forget to stay safe, post your feedback and keep smiling.
Let's start with malware. You may relate it to the word sport mentioned in the analogy above. Just as sport is an umbrella term that covers Cricket, Hockey, Baseball and so on, malware is the word that covers computer viruses, worms, Trojan, spyware, rootkit etc. In simple words, Malware is any malicious program or software designed to exploit a computer user.
A Virus in the human body is an organism that replicates itself, overwhelming body's defense mechanism and making it sick. Similarly, a program qualifying to be a computer virus must be able to replicate and execute itself. Almost all the viruses are attached to some executable file and may not affect your system unless you run or open the file. Some viruses are programmed to damage the computer by damaging programs, deleting files, or reformatting the hard disk. Others are not designed to do any damage, but simply to replicate themselves and make their presence known by popping text, video, or audio messages, which keep troubling the users. Viruses cannot spread without a human action and require transfer of an infected host file to another system for spreading.
Worms, on the other hand, are capable of spreading without human action. A worm seeks network loopholes and takes advantage of file-transport or information transport features that allow it to travel on its own. Like viruses, worms replicate themselves within a computer system but unlike viruses, a worm doesn't have to attach itself to a program. Also, worms generally localize their damage to the computer network by causing increased bandwidth.
A Trojan doesn't replicate but is as full of chicanery as the mythological Trojan Horse (of Troy). It appears to be a safe and useful piece of software but hidden inside is something harmful. While running, it may pretend to be doing something useful in the foreground but in reality, they shall work silently in the background damaging your system and/or stealing the data.
In addition to these, there are other malwares like Spywares that without your knowledge, collect your information and send it to someone who can use it.
Scarewares, which appear to be a free antivirus application but on installation proceeds to tell that system is infected with hundreds of viruses and can be cleaned only if you pay for full version.
Blended Threats, which are more sophisticated attacks bundling the worst bearings of worms, viruses and Trojans into a single threat.
Rootkits, which are designed to gain root oradministrative access to your system. I would not contempt your imagination by mentioning what harm rootkits can do.
There are more and the list keeps growing. Now you must be clear with the above mentioned terms. However, you also need to be aware of what you can do to protect yourself. Humans are generally the weakest link in the chain and unknowingly get systems affected. A little care can help you be safe, which is certainly better than being sorry. Do not click the links you are not sure about. You may install addon like WOT in your browser (firefox/chrome) which helps in identifying if a link is safe. Do not accept suspicious files or files from unknown people. Some email programs allow a "peek" into the files. Avoid even that for such files. While downloading software from internet, make sure it is from some reputed site like sourceforge or cnet.
Keep your operating system patched with latest updates. Especially if you are using Windows, get a good antivirus program and keep it updated. Don't let your firewall down. Disable auto-run in your system. Back up your important data regularly.
Share the same with your near and dear ones and if you have any more easy-to-follow points, feel free to add them to the list and mail us. We shall pass the same to the other readers of IU e-Magazine.
That's it for now. Don't forget to stay safe, post your feedback and keep smiling.
Copyrights © 2024 Inspiration Unlimited eMagazine
Any facts, figures or references stated here are made by the author & don't reflect the endorsement of iU at all times unless otherwise drafted by official staff at iU. This article was first published here on March 2012.

